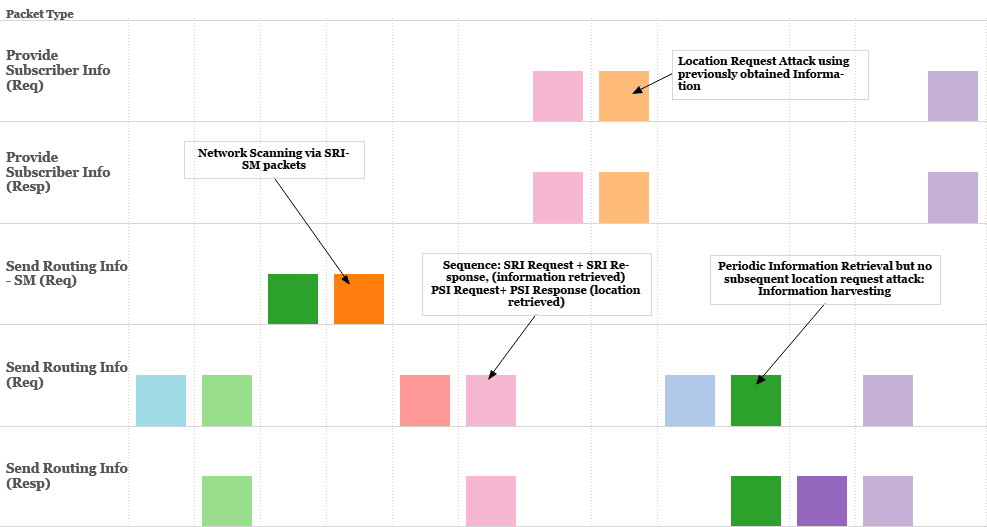
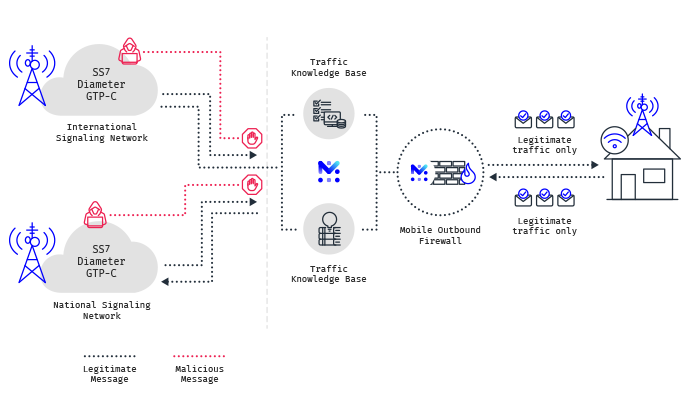
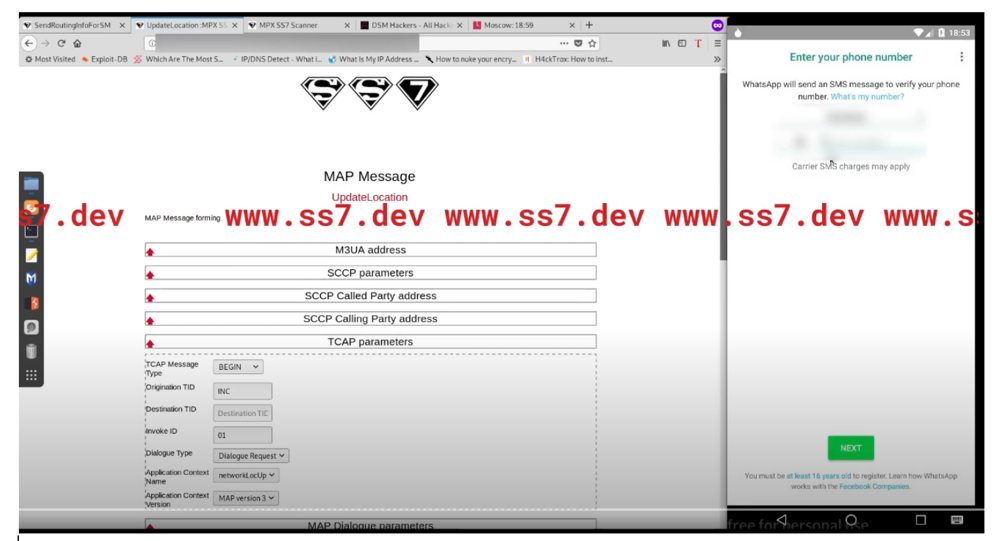
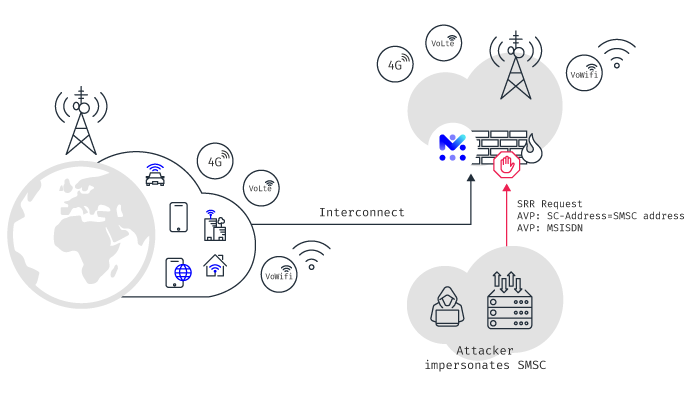
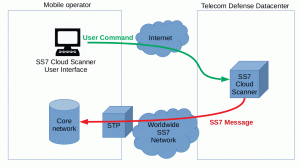
Whatsapp Hack Using SS7 Attack | Using SS7 Attack, Whatsapp accounts can be Hacked regardless of its end-to-end encryption. | By Blackphone SA | Facebook

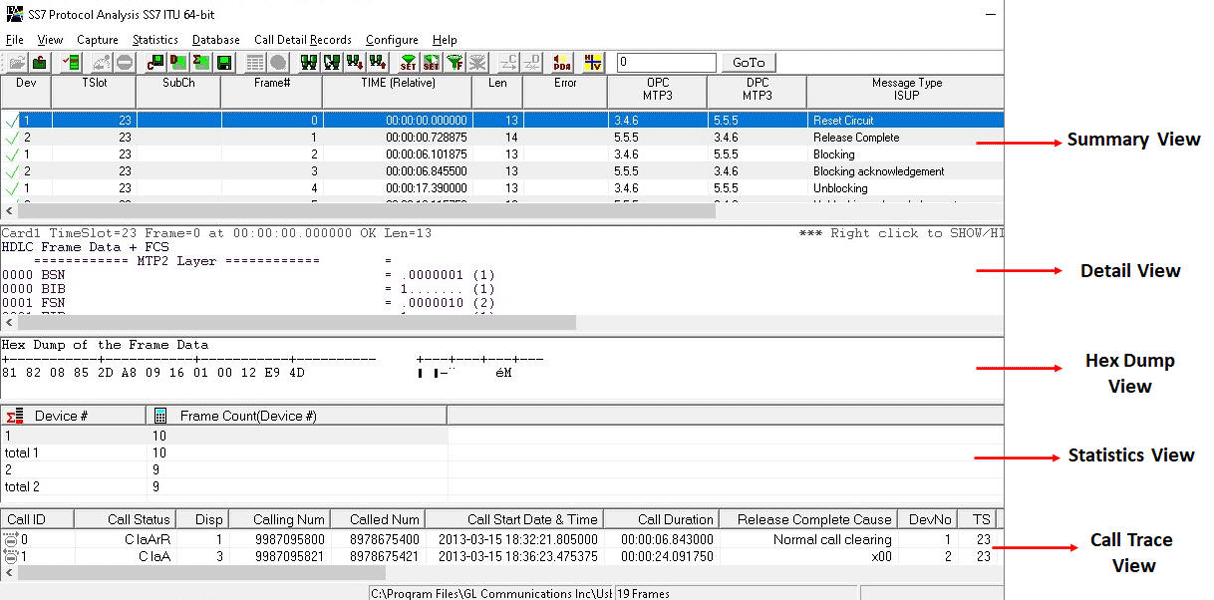
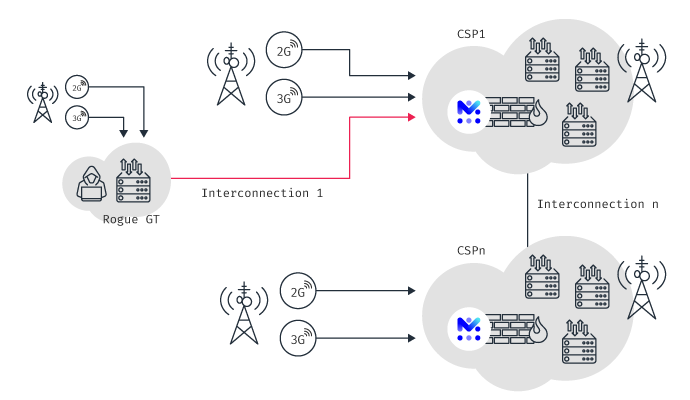
How I hacked into a Telecom Network — Part 4 (Getting Access to CDRs, SS7 applications & VLRs) | by Harpreet Singh | InfoSec Write-ups